
With extensive experience and unmatched expertise in identifying vulnerabilities across the entire spectrum, CyberSec Consulting excels in network security penetration testing. Our capabilities range from uncovering critical vulnerabilities to addressing even the most minor security gaps within your network.
At the core of our penetration testing process is a robust methodology aligned with globally recognized industry standards, including NIST, OWASP, SANS, and OSSTMM. This ensures that our testing procedures adhere to best practices, delivering a thorough and systematic evaluation of your network's security posture.

Our security consultants replicate various real-world attack vectors to identify potential vulnerabilities. This includes testing for issues such as SQL injection, cross-site scripting, and other threats.
We prioritize identified vulnerabilities based on their severity and potential impact, enabling your organization to focus on resolving the most critical issues first. This ensures optimal resource allocation for addressing risks effectively.
We go beyond quantifying risks by providing actionable insights into how vulnerabilities could impact your operations, data integrity, and reputation.
Our process doesn’t stop at identifying flaws. We provide tailored remediation strategies, actionable recommendations, and guidance to implement robust security measures that strengthen your network against future threats.
CyberSec Consulting employs globally accepted methodologies like the Penetration Testing Execution Standard (PTES) to ensure a thorough and effective assessment. Our network security testing process includes the following steps:


Comprehensive discovery of all accessible systems and their associated services to gather maximum information.

Identification of vulnerabilities using a combination of automated scans and deep-dive manual testing techniques.

Detailed documentation and analysis of identified vulnerabilities to formulate an effective attack plan.

Execution of the plan to exploit vulnerabilities and assess the real-world impact on your systems.

Detailed reporting of overall risks, including strengths and weaknesses of your security posture, for all stakeholders.
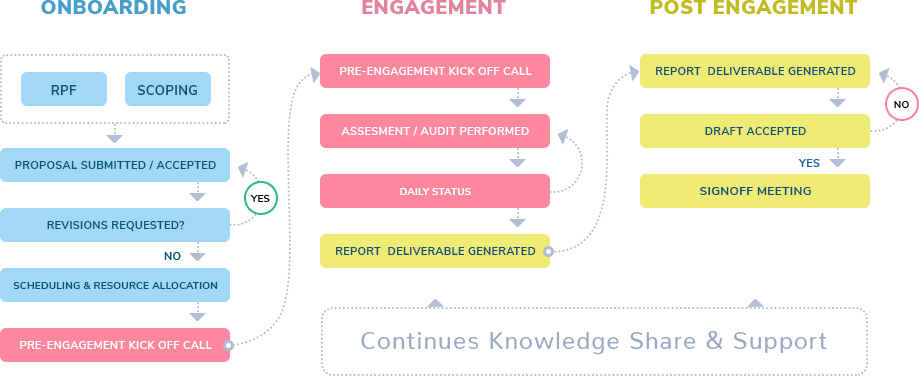
At CyberSec Consulting, we follow the following engagement workflow for working with the clients.

Wireless networks, including those using WPA2, WEP, and EAP protocols, are vulnerable to attacks that can expose an organization’s network. CyberSec Consulting identifies potential vulnerabilities starting from wireless LAN controllers to individual wireless devices.

We ensure host operating systems are secure by reviewing configurations, applying the latest security patches, and implementing best practices to fortify system defenses.

CyberSec Consulting performs a comprehensive review of your network architecture to identify gaps in existing security controls. We provide recommendations to strengthen your architecture and align it with your organization’s security objectives.
A web server is an internet-facing device, making it a prime target for attackers if not properly secured. At CyberSec Consulting, we understand that a compromised web server can cause significant damage to your business, including unauthorized modifications to user data, data theft, and the loss of critical information. To address these concerns, we offer Server Security Hardening to protect your infrastructure and mitigate risks.
Every environment is unique, and so are its security requirements. Our experts tailor a customized server hardening plan designed to enhance the security and stability of your applications. We provide 24/7 support, which includes automated checks for critical security updates and proactive notifications about hardware and operating system alerts.
Server hardening involves optimizing the server operating system to prevent unauthorized access and protect your environment. Key steps include:
These measures work together to minimize the attack surface and safeguard your server from potential threats.
Servers play a critical role in your business operations, making their security a priority. Our specialists follow industry benchmarks to ensure your servers remain secure and risk-free:
In addition to server hardening, we offer Patch and Remediation Management, covering not only operating systems but also critical software such as databases, Microsoft Office, Java, Adobe, and web browsers. Our patching module ensures your servers are thoroughly assessed for vulnerabilities, and any flaws are resolved using effective security solutions.
With CyberSec Consulting’s Server Security Hardening services, you can rest assured your servers are well-protected, enabling smooth and secure business operations.

Weak native protocols, flawed encryption designs, and common configuration errors in enterprise WLANs are among the primary reasons wireless networks are vulnerable to attacks. To address these security gaps and safeguard your business, CyberSec Consulting offers a comprehensive Wireless Security Assessment. This service helps fortify your wireless network perimeter and enhances the overall security posture of your IT infrastructure.
Backed by extensive experience in deploying and managing regional wireless networks, our experts possess a deep understanding of wireless threats, proven methodologies, and the expertise needed to secure your organization's wireless infrastructure effectively.

Gain Insight into Your Network : Understand your network structure and gather critical information to improve security.
Resolve Vulnerabilities : Identify and fix potential issues in your wireless network.
Enhance Control : Gain better oversight and management of your wireless environment.
Boost Productivity : Strengthen wireless network reliability to enhance operational efficiency.
At CyberSec Consulting, we conduct Wireless Security Assessments using documented best practices to detect and mitigate vulnerabilities. Our process includes: